Introducing Authorization Infrastructure for AI
Secure your AI systems with fine-grained authorization for RAG pipelines and agents
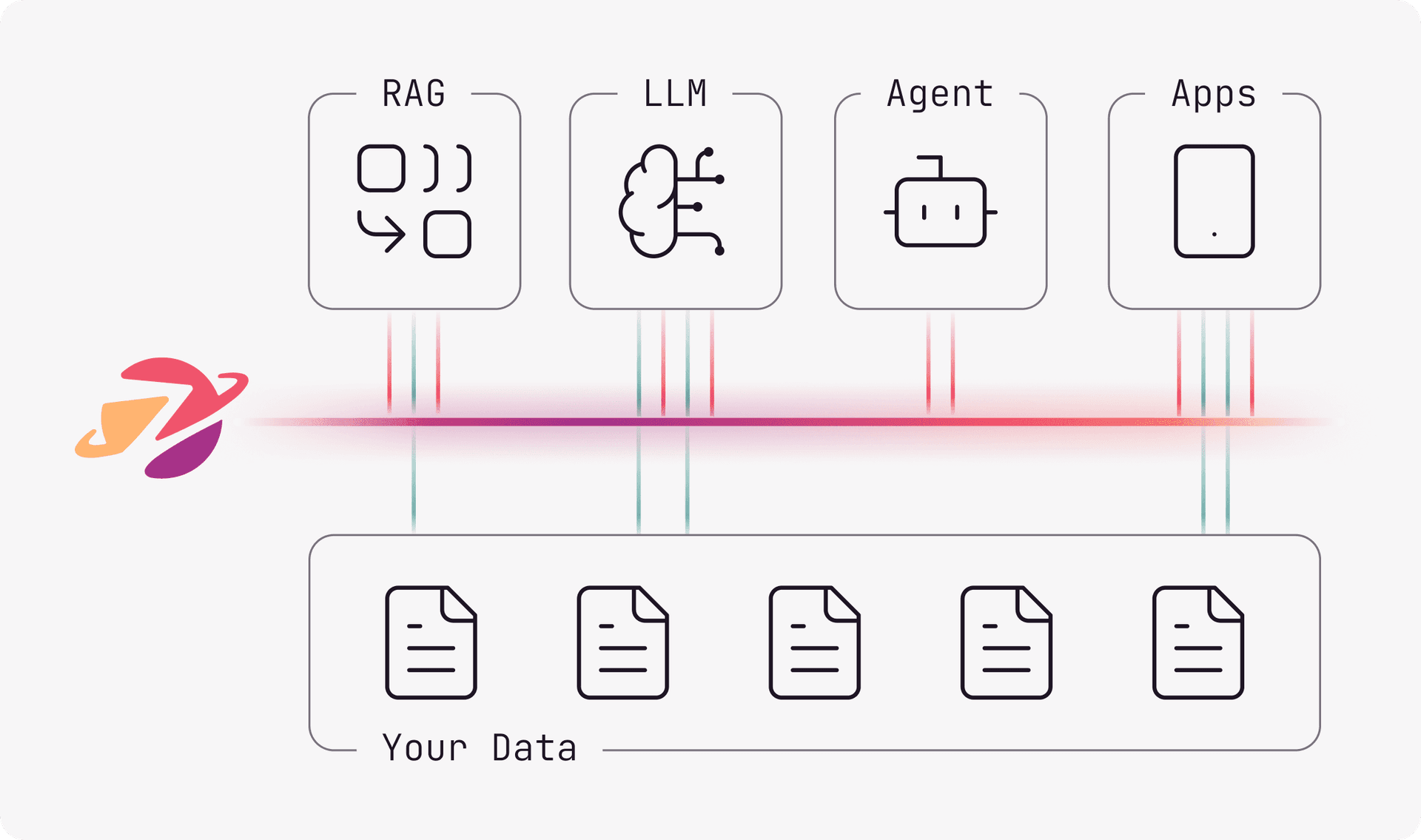
Today we are announcing Authorization Infrastructure for AI, providing official support for Retrieval-Augmented Generation (RAG) pipelines and agentic AI systems. With this launch, teams building AI into their applications, developing AI products or building an AI company can enforce fine-grained permissions across every stage - from document ingestion to vector search to agent behavior - ensuring data is protected, actions are authorized, and compliance is maintained.
AI is quickly becoming a first-class feature in modern applications. From retrieval-augmented search to autonomous agents, engineering teams are building smarter user experiences by integrating large language models (LLMs) into their platforms.
But with that intelligence comes risk.
AI systems do not just interact with public endpoints. They pull data from sensitive internal systems, reason over embeddings that bypass traditional filters, and trigger actions on behalf of users. Without strong access control, they can expose customer records, cross tenant boundaries, or operate with more agency than intended.
This is the authorization problem for AI. And it is one every team building with LLMs now faces.
Authorization for AI is not optional
When you add AI to your application, you also expand your attack surface. Consider just a few examples:
- An LLM that retrieves documents from internal systems but fails to check who is asking
- An agent that books travel but can also access payroll data
- A vector store filled with sensitive documents, exposed through approximate search
According to the OWASP Top 10 for LLM Applications, four of the top risks require robust authorization controls as a primary mitigation. And yet, most developers are still relying on brittle, manual enforcement scattered across their codebases.
We believe it’s time for a better solution.
Meet AuthZed's Authorization Infrastructure for AI
AuthZed’s authorization infrastructure for AI brings enterprise-grade permission systems to AI workloads. AuthZed has been better positioned to support AI from the get-go because of SpiceDB.
SpiceDB is an open-source Google Zanzibar-inspired database for storing and computing permissions data that companies use to build global-scale fine grained authorization services. Since it is based on Google Zanzibar’s proven architecture, it can scale to massive datasets while handling complex permissions queries. In fact SpiceDB can scale to trillions of access control lists and millions of authorization checks per second.
“AI systems are only as trustworthy as the infrastructure that governs them," said Janakiram MSV, industry analyst of Janakiram & Associates. "AuthZed’s SpiceDB brings proven, cloud-native authorization principles to AI, delivering the control enterprises need to adopt AI safely and at scale.”
Using SpiceDB to enforce access policies at every step of your AI pipeline ensures that data and actions remain properly governed. With AuthZed’s Authorization Infrastructure for AI, teams can safely scale their AI features without introducing security risks or violating data boundaries.
Securing RAG pipelines with fine-grained access control
Retrieval-Augmented Generation improves the usefulness of LLMs by injecting external knowledge. But when that knowledge includes sensitive customer or corporate data, access rules must be enforced at every stage.
AuthZed enables teams to:
- Pre-filter content before generating embeddings
- Post-filter vector search results to remove unauthorized documents
- Maintain real-time permission syncs with systems like Google Workspace or SharePoint
- Build permission-aware retrieval layers that balance relevance with compliance
Whether you are building with a private knowledge base, CRM data, or support logs, SpiceDB ensures your AI respects the same access controls as the rest of your systems.
Governing agent behavior with clear permission boundaries
AI agents are designed to act autonomously, but autonomy without boundaries is dangerous. With the AuthZed Agentic AI Authorization Model, teams can enforce clear limits on what agents can access and do.
This model includes:
- Functionality Control: Define and restrict which tools an agent can use
- Permissions Management: Apply inherited user permissions to agent behavior
- Autonomy Oversight: Introduce approvals for high-impact actions and maintain full audit logs
Whether your agent is summarizing data, booking a meeting, or triggering a workflow, it should only ever do what it is explicitly allowed to do.
What this looks like in practice
Let’s say an employee types a natural language query into your internal AI assistant:
“What was our Q3 revenue?”
Without authorization, the assistant might retrieve sensitive board slides or budget drafts and present them directly to the user. No checks, no logs, no traceability.
With AuthZed:
- The system checks the employee’s permissions
- Only authorized financial data is retrieved
- An audit log is created for compliance
- AI operates with the same access controls as the rest of the application
This is what AuthZed’s Authorization Infrastructure for AI makes possible.
Built for builders
You should not have to choose between building smart features and maintaining secure boundaries. With AuthZed:
- Authorization integrates into your AI stack in minutes, not months
- SpiceDB scales with your users, tenants, and access models
- RAG and agent systems become extensions of your existing permission architecture
And it is already being used in production. Workday uses AuthZed Dedicated to secure its AI-driven contract lifecycle platform. Other major AI providers rely on SpiceDB to enforce permissions across multi-tenant LLM infrastructure.
Get started quickly
If you are building AI features, AuthZed’s Authorization Infrastructure for AI helps you ship faster by allowing you to focus on your product, instead of cobbling together an authorization solution. Whether you are securing vector search, gating agent behavior, or building out internal tools, AuthZed provides the authorization infrastructure you need.
- Check out the AuthZed [Authorization Infrastrructure for AI solutions page]
- Try the open-source RAG security workshop on GitHub
- Try the open-srounce AI agent authorization workshop on GitHub
- Learn more from Sohan and Evan from our team about securing your RAG pipelines with fine grained authorization
- Book a demo with our team