Authz and Authn, a primer
As humans, we’ve been guarding our stuff since we first invented locks 6,000 years ago.
Guarding assets and sharing access to them is human nature. There are two major steps involved in this process: authentication and authorization. First, one must authenticate that they are who they say they are. Then, once someone’s credentials verify their identity, the next question is whether or not that individual is allowed access to the asset.
Think of it this way:
You want to go on a trip to another country. You need a passport to verify that you are who you say you are - this is an example of authentication. You also need a visa that gives you permission to enter the other country. This is an example of authorization. The same principles can be applied in computing:

Authorization and authentication get confused OFTEN - I mean, look at how similar the words are! Instead of having the perspective of authentication vs. authorization, let’s understand how they work together. As you’ll see, you can’t have one without the other.

Authentication
What is Authentication?
Authentication, in computing, involves verifying the identity of a user, process, or machine. To authenticate a user, we can use one or a combination of three key factors:
- Knowledge: Something a person knows – i.e. a password/username, a passcode or PIN, or a security question
- Ownership: Physical token or something a person owns – i.e. a Yubikey, hardware capable of an encrypted handshake (like ACME for Apple devices), or Google Authenticator
- Inherence: A vital piece of something a user is or does – i.e. biometrics or keystrokes
Whenever you sign into social media, your email, or any Web-based application, you are using authentication to prove you are who you say you are.
The History of Authentication
Authentication has been a part of our world since the dawn of time, but that is another conversation for another day. For now, let’s dive into the history of authentication in modern computing.
Authentication started all the way back in the 1960’s (60 years ago!) with the first passwords in databases. From there it moved to passwords with a hash, and eventually, encryption. Modern encryption has been around since the 1970’s with RSA asymmetric encryption.
Timeline
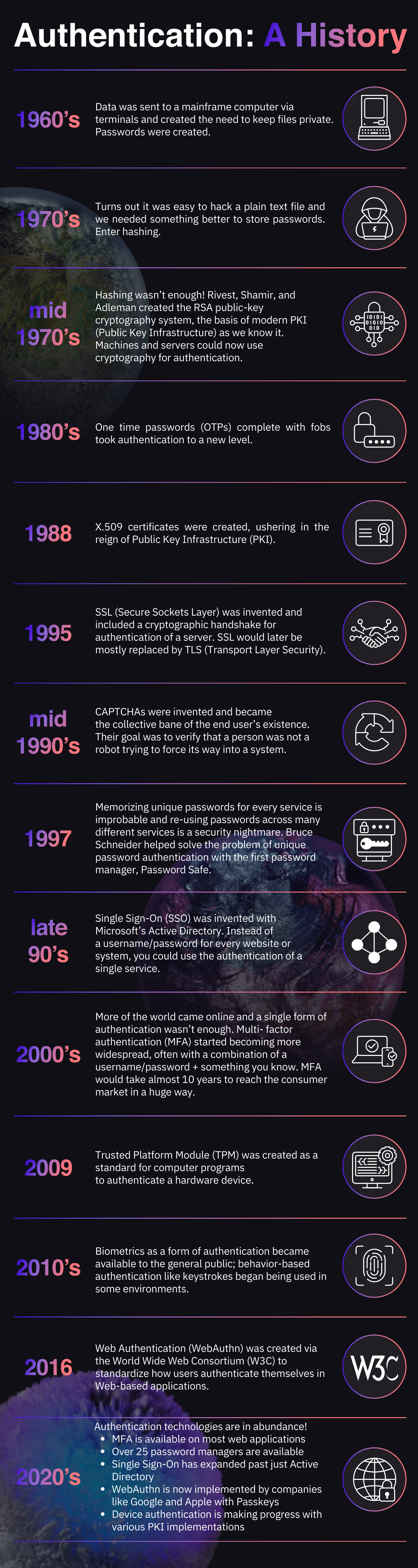
[Timeline is based on an excellent piece - “Digital authentication: The past, present and uncertain future of the keys to online identity” on GeekWire, with a few new additions by the authors]
We don’t know where authentication will go in the future but as technology continues to advance, the ability to identify an individual user will get more complicated. This rings true for all Web applications and services, but even more so for highly secure or zero trust environments such as government platforms and healthcare data. Authentication is the passport to our digital world.
Authorization
If authentication is our passport, authorization is our visa. Authorization is when one entity grants permission to another entity to engage with a resource within a set of boundaries. Authorization has become increasingly difficult for application developers, often causing performance issues when deployed at scale and blocking feature development.
As our digital footprint has grown, experts have developed new access control and permissions management models to meet the needs of feature hungry teams. Since the advent of the original Access Control List Model (ACL) in the 1960s – similar to an “invite only” guest list – we have designed increasingly abstract authorization systems.
Timeline
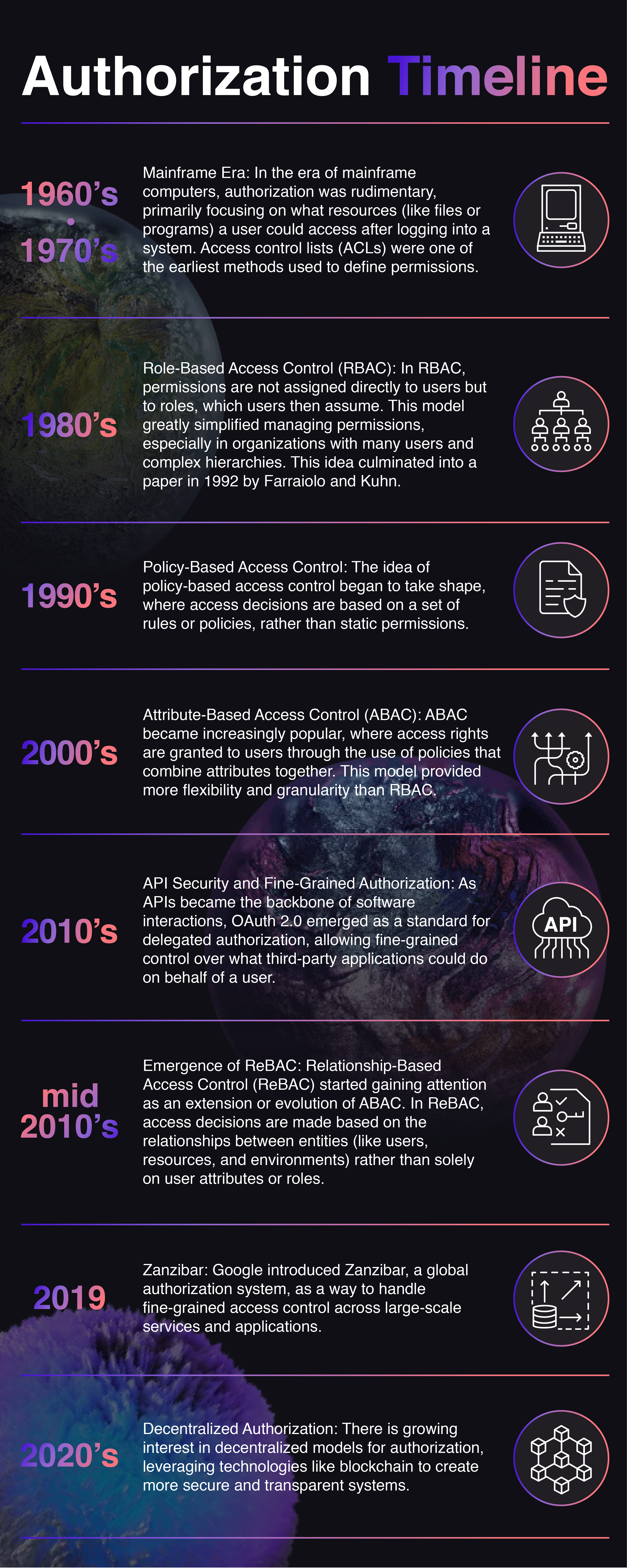
Moving forward, interest will likely trend toward dynamic, context-aware systems that can adjust permissions in real time. The exploration of decentralized models for authorization that integrates concepts from ReBAC and systems like Zanzibar suggests a future with more secure, efficient, and flexible access control mechanisms.

As technology develops, so will both authentication and authorization. We at AuthZed are excited to be on the forefront of the authorization space, bringing Google’s Zanzibar to the masses with SpiceDB.
You can try out a schema here and get started with fine-grained access control across all of your environments and applications.

